Golden Dome Will Run on Data: Cross Domain Sharing Is Essential for Missile Defense
By: Petko Stoyanov, VP of Product Strategy at Everfox
The United States Department of Defense (DOD) appears to be moving quickly to stand up Golden Dome: a layered homeland air and missile defense system that blends space-based sensing, ground and maritime interceptors, and an integrated command and control fabric. Recent reports indicate an ambitious timeline, with early demonstrations planned before the end of the decade.
None of that will matter if all of Golden Dome’s data cannot move, be trusted, and be acted upon in time. Golden Dome will succeed or fail based on how well it shares, filters and protects information across domains, agencies and classification levels.
The real bottleneck is the boundary
Sensor and shooter technologies are familiar territory to the DOD. These systems encounter friction when networks at different domain and classification boundaries need to be interoperable. Consider a realistic scenario: a Navy ship detects a launch, space sensors refine the track, ground radars contribute discrimination, a joint battle manager fuses the inputs and tasks the right shooter and civilian or allied stakeholders receive a releasable picture.
Every step crosses a boundary with different owners, enclaves, protocols and classifications. Each boundary exists to block data leakage and cyber intrusion, yet they can also delay information sharing, require manual re-entry or cause brittle, one-off connections. In a saturation attack or mixed raid, those inefficiencies multiply and risk jeopardizing the system’s effectiveness.
Data must cross these boundaries at the required speed. Kill chain latency will likely be the most important non-functional requirement of the Golden Dome system. As such, the system’s architecture must budget sub-second latency for sensing, fusion, adjudication and tasking, then back-propagate those budgets to each boundary crossing. Further, it will need to facilitate sub-second guard transit for structured data, such as track messages and engagement status.
Golden Dome will also need to transfer data for larger products, including sensor snapshots and classifier features, using pre-approved templates in seconds, not minutes. And it will require deterministic fail-over to alternate paths if a node degrades, as well as accommodations for burst behavior.
Additionally, Golden Dome’s RAID density will matter more than its steady-state throughput. The network will need to engineer guards and messaging layers for peak message rates with margin and then prioritize them by mission value, not first-in first-out.
It is clear Golden Dome’s most difficult engineering problem is not developing a new interceptor; it’s moving the right data to the right place with mission-critical cybersecurity and low latency to make the system functional.
Cross domain solutions are a proven, functional bridge
Golden Dome is not a single system. It is an evolving system of systems, meaning its data layer must scale across thousands of nodes and accommodate frequent change.
The DOD and the Intelligence Community are already using Cross Domain Solutions (CDS) as a bridge to move information between isolated networks while enforcing security policy. These capabilities are advancing to meet the scale and assurance that programs such as Golden Dome will demand, and for such an application, it should be treated as first-class infrastructure.
In the context of Golden Dome, CDS can be designed to fuse multi-source tracks in near real time through one-way flows from high-side sensors to operational systems. CDS can also automate release and sanitization with machine-enforced rules that remove sensitive fields and publish releasable products to partners.
Critically, CDS can prevent protocol and content cyberattacks through deep inspection, transformation and protocol breaks. CDS can be standardized on a small set of patterns and deployed at predictable choke points across the architecture rather than creating bespoke guard pairs. This approach would simplify accreditation and operations at scale.
AI needs CDS, too
Golden Dome will also need to leverage AI/ML to correlate tracks, classify threats and recommend fire control options. Those models need diverse data. Without CDS, you either starve the models or clone data into every enclave and accept drift and cost.
However, with CDS, AI/ML models can be trained with rich, high-side data and then publish outputs and artifacts that are safe to run on lower domains. (Figure 1) CDS can selectively pass only approved features or embeddings across domains, not full raw data, and can publish labeled exemplars through a sanitization pipeline to continuously calibrate lower-side AI/ML models.
These safe AI/ML models can be tied back into the command-and-control fabric with the same guard rigor used for human-generated products. If a model flags a decoy or a hypersonic maneuver pattern, that advisory can traverse domains with the same policy enforcement and audit in operator reports.
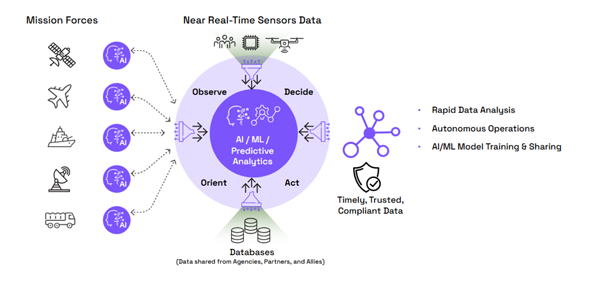
Enforce Zero Trust at every boundary
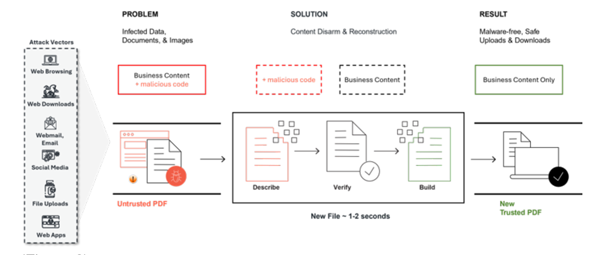
Golden Dome will be a prime cyber target. A Zero Trust posture will be required via a set of controls at each boundary crossing, which CDS can enable by tying strong identity to the process level and binding flows to workloads and signed software, not just to hosts or subnets. CDS also enables content disarm and reconstruction to deconstruct active content, verify what is legitimate and construct files into safe forms by default. (Figure 2) Additionally, CDS allow for continuous inspection and recording so that every transfer decision and payload hash can be logged to support incident response and after-action analysis.
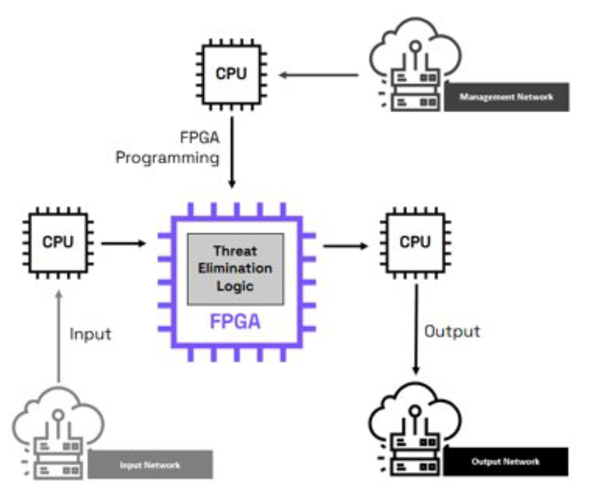
CDS also accommodate the use of hardware-enforced security policy to raise assurance via one-way data transfer where applicable. This places portions of the guard decision logic within tamper-resistant components (Figure 3), shrinking the attack surface for software exploits and increasing operator confidence.
Golden Dome can expect a steady flow of coalition and civilian interfaces from organizations including NORAD, FAA, DHS and trusted foreign partners. The data release problem presented is two-sided: protecting U.S. sources while honoring partner security restrictions.
CDS can preserve Zero Trust policies of the various involved domains, even extended into partner environments. This includes enforcing bidirectional release control for both “U.S. to partner” and “partner to U.S.” security policies with separate rule sets and audit trails. CDS provide label-driven routing that leverages data labels and caveats to automatically steer products to the correct enclaves. It also allows for deterministic redaction to provide predictable sanitization so partners can build to it and reduce human arbitration in the loop.
Closing thoughts
Operationalizing a system as vast and comprehensive as Golden Dome can benefit from commercial off-the-shelf (COTS) components that can shoulder the load of a national-scale missile defense shield. Here, certain CDS have the capability for:
- Enterprise-class messaging for pub/sub and event streaming that already meets throughput and reliability targets.
- Fieldable guard appliances that meet NCDSMO Raise-the-Bar and have existing ATOs, shortening the path to production.
- Security-hardened browsers and isolation technology, letting operators work across enclaves from one seat while maintaining separation.
- Proven observability stacks for telemetry, tracing and capacity planning.
Pairing COTS with clear acceptance criteria will be essential. If a component cannot meet jitter, determinism or inspection requirements, it should be excluded from the critical path and used for non-time-critical products.
While the system’s hardware will draw significant attention during development, Golden Dome’s outcomes ultimately hinge on secure and rapid data access and transfer.
If the program includes cross domain data sharing, Zero Trust enforcement and hardware-logic enforced cybersecurity policy from day one, it can meet the aggressive deployment timeline and the sensors, AI/ML, and interceptors already on the table can perform as a coherent defense when it counts. On the other hand, if those elements arrive late, the shield risks becoming a set of impressive but disconnected and ineffective pieces.
