Advancing the Internet of Military Things (IoMT) with Software Defined Radio
Discussed in this article are the many technologies involved in handling the vast amount of data generated by the IoMT/IoBT devices, including tactical edge servers and software defined radio (SDR). A great deal of challenges exist for these networks, including security, bandwidth, storage and processing limitations.
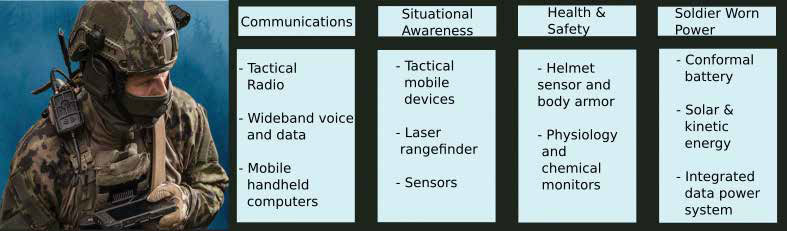
Information on the battlefield is becoming more and more critical to the success of mis-sions. Recognizing this, military’s around the world, and especially the US Military, are looking to the internet of military things (IoMT) or inter-net of battlefield things (IoBT). Broadly speaking, IoMT/IoBT is part of the persuasive/ubiquitous computing paradigm; a complex network of various sensors, actuators, and devices found on the ground, sea and in space which provide information technology for combat operations, reconnaissance, and even warfare capabilities.
Distributed IoMT technology includes those found on UAVs, drones, robots, human wearable devices, biometric devices, weaponry, armour and a host of smart technologies. With IoMT and the ability to connect ships, planes, tanks, drones, soldiers, and operating bases in a close-knit network, the military greatly benefits in in-creased situational awareness, risk assessment, and response time. The use of these devices is based on the idea that battles will be fought and won based on who has the most intelligence, cyber warfare capabilities and overall machine intelligence, which may even someday perform autonomously.
Types and Benefits of IoMT/IoBT Intelligence and Sensing
There are various advantages, increased capabilities, and benefits accrued from these types of networks of sensors, including the following for
ground, air, and sea military services:
1. Ground:
- Sensing and computing devices can be worn by soldiers and embedded in their combat suits, helmets, weapons systems, goggles and other equipment
- These wearable systems are capable of acquiring a variety of static and dynamic biometric data including facial expression, eye movement, fingerprints ( for instance, drone controller authorization), heart rate, gait and stance, and gestures.
- Soldiers are able to obtain fingerprints from a weapon or bomb and upload it to the network in order to identify an adversarial combatant instantly.
- Images or visuals of an adversary can be uploaded to a database to confirm the identity of a
- target.
- Soldiers exposed to toxic chemicals, injured in battle, etc. can receive medical assistance.
- One such example is the NSRDEC (Now CCDC) Connected Soldier program.
2. Air:
- Drones, UAVs, fighter jets, helicopters, you name it; all can provide visual data on a suspected area harbouring adversaries.
- Information relayed from military air craft to ground troops can allow for safe entry into an area or recognize if this is an area needing aerial artillery support or other measures.
- Edge computing lets soldiers gain access to vehicles and weapons systems as well as monitor battlefield conditions through connected drones.
- Assessing pilots under abnormally high G-force conditions is also possible with sensor technology.
- One such program is the US Air Force’s Advanced Battle Management System (ABMS).
3. Sea:
- Unmanned flotillas mapping or detecting enemy vessels, and other ocean situational awareness, to ensure safe passage of naval or commercial vessels.
- Surveilling coastlines, while sending data to satellites in order to be relayed to other military branches or command and control (C2).
- Able to obtain ocean temperature and ocean state measurements and upload data to cloud based networks to warn of potentially threatening weather.
- One such example is the Defense Advanced Research Projects Agency (DARPA) Ocean of Things program.
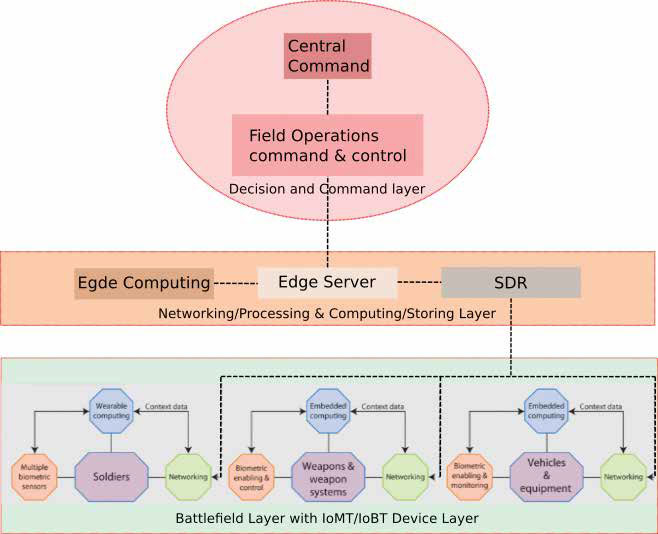
Networking: How Information is Relayed to/from Command and Control (C2) and the Battlefield To gather intelligence and communicate with IoMT devices and the various military branch-es, a central C2 is necessary with network connections to various military branches and the various IoMT/IoBT devices and sensors. The end-to-end communication of a geographically dispersed set of information and radio capabilities for sensing, transmitting/receiving, collecting, processing, storing, disseminating and managing information on demand to military personnel, commanders, policy makers and others, is a great technical challenge.
Modern radio technologies used in IoMT/IoBT transmit/receive functionality is based on soft-ware-defined radio (SDR). This is a radio system where RF communication is done using software/firmware, instead of hardware that traditional radios were based on. Importantly, signal process-ing tasks for modulating/demodulating and/or encoding/decoding C2 communications, video, images, audio, biometrics, and all IoMT/IoBT sensor and device data is sent using the SDR portion of IoMT/IoBT. SDRs also play a prevalent role for feeding data via a high throughput physical link to the servers which process, store, and connect all of C2 networks and subsidiary networks.
One such networking system widely used in IoMT/IoBT is cloud computing; used to offload immense amounts of data onto servers with far greater processing power than would otherwise be achievable on a local machine. This is only effective until you get to the tactical edge, i.e. on the battlefield, where mission requirements are dynamic and fast changing, and where the need for computing power and speed is great but network/radio communications are challenging in transferring cloud data; specifically in regards to limit-ed network bandwidth and high network latency.
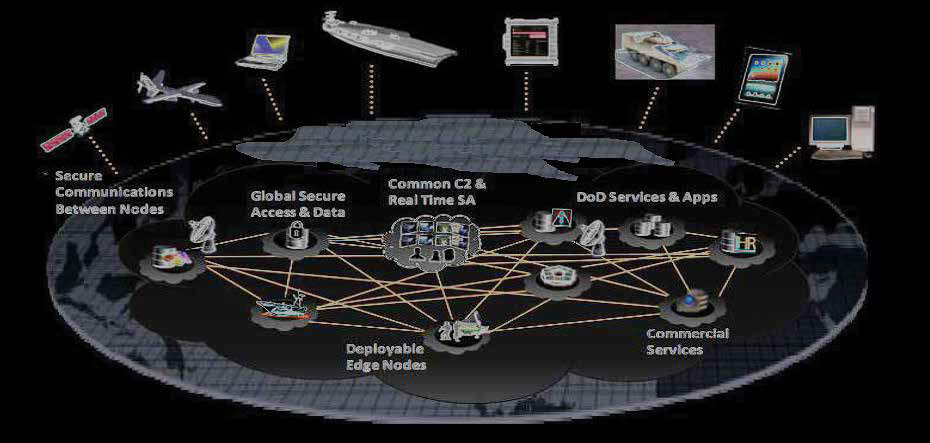
A key element of IoBT/IoMT network infra-structure, then, is a strong edge computing architecture that uses data from biometric wear-ables, environmental sensors, video cameras, microphones, and other connected devices, and processes, sends, and receives data quickly, allowing military personnel to respond to potentially dangerous or life threatening situations on the battlefield. Tactical Edge servers or “cloudlets” are the backbone for data-generating clients and IoMT/IoBT devices on or near the battlefield, using the alluringly efficient, divide-and-conquer edge computing architecture. This collection of real-time data and information dissemination rely on uninterrupted connectivity of the network, which is vital in allowing the IoMT/IoBT to maximize potential. This includes the ability for edge-based tactical networks to share data in real time between a dynamic net-work of impromptu nodes (IoMT/IoBT devices) that may come and go over time. One such communication standard for this real-time network edge computing scheme is data distribution service (DDS). An overview of the connectivity lev-els in shown in Figure 3 on next page:
IoMT networks disseminate collected data over radio signals which establish and maintain mobile and uninterrupted C2 communications between operational elements, including those in battle on the ground, air or sea, as well as higher central command headquarters (Figure 3). Radio devices are designed to provide in-teroperability with all services, various agencies and military of the U.S. Government, and allied coalition forces.
Often these networks of IoMT/IoBT devices cre-ate an overwhelming amount of data for the sys-tem. To prevent this overloading, often intelligent data filtering is used; allowing for data acquisition from IoMT/IoBT devices to not overwhelm the computational capacity of servers. Other meth-ods to prevent overloading include using net-work function virtualization (NFV). NFV offers the operator the ability to configure the network infrastructure dynamically through a protocol management system. Hence, NFV empowers C2 to quickly configure data links for changing oper-ational needs, and to manage device and data se-curity throughout the system. This could include giving priority to certain radio/data channels coming from a battlefield’s IoMT/IoBT devices and sensors, if they are requiring immediate assis-tance or an emergency situation.
One such example of NFV is found with how drones can transmit video in rural areas with the support of a software defined network (SDN) en-abled backbone with virtual network function (VNFs). By re-encoding the video transmission, the distributed NFV services can adapt the video qual-ity based on bandwidth constraints, while service function chains (SFC) within the SDN can be rout-ed to select the most appropriate network path.
Other networking includes device-to-device (D2D) and edge-to-edge, for which is more suit-able for ground-based soldiers requiring the use of an IoMT/IoBT device. More options include device-to-cloud, for such applications as verifying a target identity, or edge-to-cloud, for off-loading data to the cloud network.
While IoMT/IoBT is a promising technology, the sheer amount of sensor and device data be-ing acquired across all military branches, means that much of this data is not accessible by various military branches in real-time. To help solve this, the Department of Defense (DOD) created the Joint All-Domain Command and Control (JADC2) program, a multi-billion-dollar pro-gram to revitalize the military’s current C2 infra-structure by establishing a harmonious network of sensors, devices and warfighters that enables collective, real-time decision-making across the US Air Force, Army, Marine Corps, Navy, and Space Force branches. This will differ from how previous generations of networks for IoMT/IoBT have had their own tactical network which was largely incompatible with one another or required significant time delays when accessing data from diffuse networks. The JADC2 network will allow far more readily available and accessible information, such as reconnaissance and surveillance, from a variety of military forces networks. The idea is to provide greater collective situational awareness, or creating a common operating picture (COP) of an area of conflicts, thereby providing a means for much quicker decision making.
Other Challenges and Requirements for IoMT/IoBT Besides an overload of data, IoMT/IoBT net-work infrastructures are often limited by frequent disconnections, network partitioning, and fluctuations of radio channel conditions in which the devices are transmitting/receiving data. This can lead to issues in sensor or device availability and constraints on the usage of such devices. Moreover, there are many challenges with respect to how to manage, process and share the data in systems containing edge or cloud networks, limited computing resources, limited network band-width and where connectivity to C2 systems is not always guaranteed. Data filters, edge device regulation, and network upgrades can be used to combat these issues via increased maximum bandwidth, however, this is only part of the solution to a vast array of problems. One other broad problem of IoMT/IoBT net-works is security. The more devices on the net-work, the more exposed is the network to cyber attacks; an obvious fact of IoMT/IoBT networks. Attacks include denial-of-service, spoofing (presenting false data from what is seen as a reliable source), and even exposing accelerometer sensors to fake movements using acoustic interference, bypassing authentication mechanisms in drones, and many other issues. IoMT/IoMT devices themselves pose a challenge. The capabilities of the device/sensor nodes are also often limited by low battery life, low storage capacity and limited CPU power. While battery technology has improved over the years, often the only way to allow for long duration missions requiring IoMT/IoBT is to use solar power generators or other forms of renew-able energy. Of course, this also leads to another issue: more equipment needing to be carried out on the battlefield.
The main challenges for IoMT/IoMT radio communications are due to wireless communication links being directly exposed when de-ployed in combat, resulting in various cyber or physical attacks threatening network connectivity. Therefore, the ability to maintain network connectivity under adversary attacks is a critical property for the IoBT and one that is not easily solved. Issues relating to jamming, and various electronic warfare (EW), make it particularly challenging yet necessary to mitigate attacks on these networks. Well-known attacks on radio de-vices are spoofing, eavesdropping, side-channel, jamming, and replay; all of which are based on exploiting the vulnerabilities present in radio devices and/or communication protocols. This creates serious disruptions to mission critical IoMT/IoBT devices.
Adversaries have become more advanced in their ability to know how electronic devices, used by the military, function at a very low level. Recognizing the threat of this, DARPA created the Trusted Integrated Circuits program resulting in the development of technologies that ensure reliability in the manufacturing process of electronic devices used in military systems. As well, DARPA’s Microsystem Technology Office (MTO) ensures the provenance, security, and reliability of electronic components driving the critical military capabilities of the coming decades.
SDRs for IoMT/IoBT SDR technology provides a more scalable and extensible radio system in comparison to a system composed of dedicated hardware. This is particularly important for IoMT/IoBT applications, as most updates are simply software upgrades— providing the capability to upgrade radio protocols or even introduce new functionality into an IoMT/IoBT device remotely. These systems are also able to be constructed in many form factors, and be deployed in the IoMT/IoBT devices themselves, as well as the radio portion before edge computing or cloud computer servers. In this configurable, they can provide necessary modulation/demodulation and encoding/decoding required for radio communications to these devices.

Moreover, to prevent issues related to adver-sary EW, SDRs can constantly hop from one fre-quency to another to avoid congestion or, more importantly, to avoid enemy jamming. Other security measures include the ability of the on-board field-programmable-gate-array (FPGA) to encrypt/decrypt radio communications. SDRs are also able to provide EW and cyberattack capabilities against the adversary when need-ed. This can include providing a means to jam or spoof adversary equipment, such as a device lying on GPS/GNSS signals, to ensure military assets are protected. Ruggedized SDRs can be paired with ruggedized edge server systems for battlefield process-ing of IoMT/IoBT data. The high throughput of data ( from 10 – 100 GBps) made possible with high performance SDRs, such as Per Vices SDRs (Figure 4), provides a means to connect all the many devices in the battlefield. Moreover, the multiple-input multiple-output system allows for receiving and transmitting signals across multiple carrier frequencies, and thus allowing for one device to control a host of radio communication for IoMT/IoBT devices.
Conclusion
IoMT/IoBT is an ongoing development which can provide immense capabilities but also re-quires addressing a number of issues outlined in this article. One promising technology used extensively in this field is SDR. The benefits of these systems are numerous and will continue to push the frontiers of IoMT/IoBT system development. The key takeaway message is that SDR for IoMT/IoBT will stand the test of time as new functionality is required on the battlefield.
References
- https://www.ncbi.nlm.nih.gov/pmc/articles/PMC5087432/
- https://www.prnewswire.com/news-releases/sri-international-leading-security-research-for-us-army-research-lab-initiative-to-develop-and-secure-the-internet-of-battlefield-things-iobt-300601689.html
- https://www.computer.org/publications/tech-news/research/internet-of-military-battlefield-things-iomt-iobt
- https://www.researchgate.net/publication/327709145_Combat_Cloud-Fog_Network_Architecture_for_Internet_of_Battlefield_Things_and_Load_Balancing_Technology
- https://www.japcc.org/wp-content/uploads/Read_Ahead_2020_Screen.pdf
- https://www.trentonsystems.com/blog/tactical-edge-servers-helping-the-military
- https://www.trentonsystems.com/blog/what-is-jadc2
- https://www.omg.org/news/whitepapers/DDS-Tactical-Edge-Whitepaper.pdf
- https://www.darpa.mil/program/ocean-of-things
- https://www.sciencedirect.com/science/article/pii/S1319157821000896
- https://www.mdpi.com/1999-5903/10/9/88/pdf
- https://www.microwavejournal.com/articles/34577-sdr-in-military-and-aerospace—beyond-tactical-radios
- https://militaryembedded.com/radar-ew/signal-processing/expanding-software-defined-radio-versatility-for-the-digital-battlefield
- https://onlinelibrary.wiley.com/doi/pdf/10.1002/hbe2.231

